Creating manual keytab file for Imprivata and VMware Workspace One Access.
When using VMware Horizon, VMware Workspace One Access, TrueSSO and Imprivata you need to enable Kerberos Authentication within Imprivata and a new created keytab file. Imprivata provides the application isxkerbul.exe to fix that but you can do it manual with ktpass.
This can be use full when you are using custom name convention.
When u are using the isxkerbul.exe application it will make a remote admin share on the Active Directory server and removes it when finished this is not something I like to happen so I create it with ktpass.
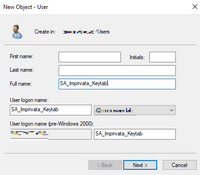
When you are creating the keytab file you will need a domain account with the Service Principal Name (SPN) of the appliance for example: SA_Imprivata_Keytab.domain.xxx
There are some rules that apply.
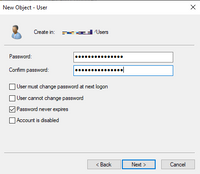
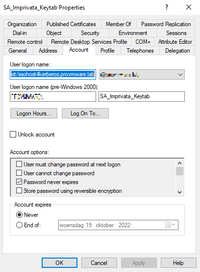
- User must change password at next logon, not apply
- Password never expires, apply
- Account Name with no spaces
There are some rules that apply to the Imprivata appliance to.
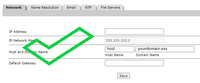
- Appliance host and domain name should be written in lower case in the appliance console.
- Configuring Network Protocol Time (NTP) servers makes sure that the Kerberos ticket does not expire before the appliance can extract the user identity from the Kerberos ticket.
After creating the account you can create the keytab file its time to Rumble!! No ;-) to create the keytab file:
Run a command prompt as Domain Admin.
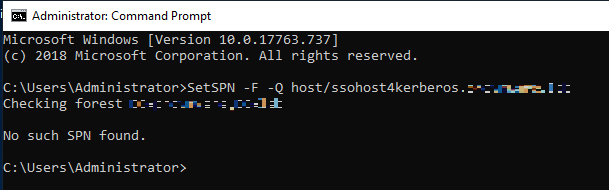
check if the SPN is not already used: SetSPN -F -Q host/ssohost4kerberos. yourdomain.xxx
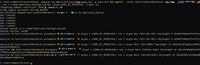
To create the Keytab file use the following command: ktpass -mapuser SA_Imprivata_Keytab@ yourdomain.xxx -pass “password Keytab account” -princ host/ssohost4kerberos.yourdomain.xxx@YOURDOMAIN.XXX -out C:\temp\Imprivata-OneSign.keytab -ptype KRB5_NT_PRINCIPAL -crypto ALL
The SPN formatting explaned:
before the @ = lower case (host/ssohost4kerberos.yourdomain.xxx)
after the @ = upper case (YOURDOMAIN.XXX)
- This is due to the way Unix stores the realm value, which is also in uppercase.
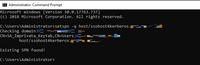
To check if the account is created with the SPN, type the following:
setspn -q host/ssohost4kerberos.yourdomain.xxx
When you check the user account the changes are made within the Active Directory.
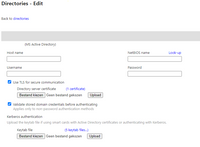
Upload the keytab file to the Imprivata appliance manual.
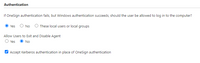
And don’t forget to enable the Kerberos computer policy within Imprivata OneSign.
I'm not the first one to blog about this, Edwin de Bruin also created a blog about how to create a keytab file a while ago only this one is about the Imprivata tool isxkerbul.exe: debruinonline
Thank you for reading if you have a question, remarks? Please let me know!